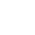
In the summer of 2014, I graduated from University of Delhi with a Bachelor’s degree in Journalism. Part of my graduation requirement was working on an undergraduate thesis that looked at contemporary issues within the media industry. My piece was titled “Technology Journalism In The American Online Media: Reporting Matters Of Money, Products And Policy.” The 18,000-word dissertation picked up specific cases to illustrate the three themes. For policy I looked at the coverage of Edward Snowden’s NSA leaks.
The data set wasn’t mainstream media but native digital publications focusing on technology. In this case – TechCrunch, The Verge, Gigaom and Engadget. As the NSA controversy continues to be at the centre of the media’s discussion and first amendment issues are at the realm of several media debates, the third chapter of my dissertation looked at how exactly did these websites cover the initial bits when The Guardian and Washington Post broke the story. In a media space that ages quickly, it might not be best to publish something that was written in April 2014 in October 2014. Yet, here is the entire text of a chapter from my undergraduate thesis.
P.S.: With the footnoting and the long paragraphs, I know this isn’t exactly meant for the web. Kindly bear with that bit.
“I don’t want to live in a world where everything that I say, everything I do, everyone I talk to, every expression of creativity, or love, or friendship is recorded, and that’s not something I’m willing to support, it’s not something I’m willing to build, and it’s not something I’m willing to live under.” – Edward Snowden
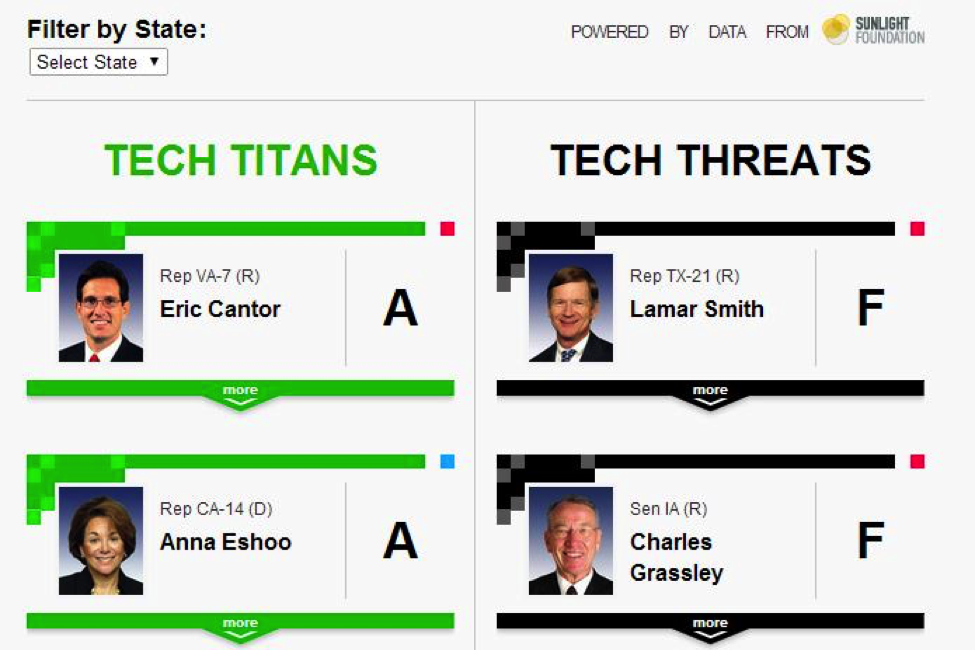
The 2014 Pulitzer Prize for Public Service has been awarded to the Washington Post and Guardian U.S. One of the journalists behind this award winning story – Glenn Greenwald, labeled it as “the biggest intelligence leak in a generation, if not ever,”[1] and in many ways, it is much rightly so. It started with a report published by the US edition of the British paper Guardian on June 5, 2013. According to the same, the National Security Agency (NSA) – the biggest intelligence agency under the US government was mass storing private data of Internet and mobile users around the world.
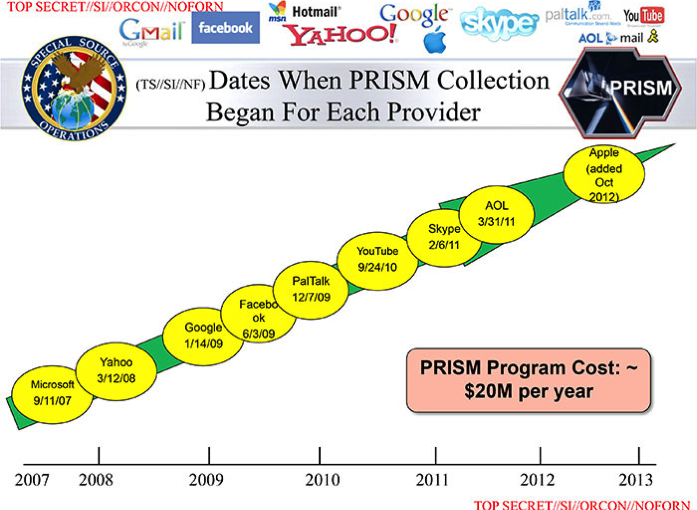
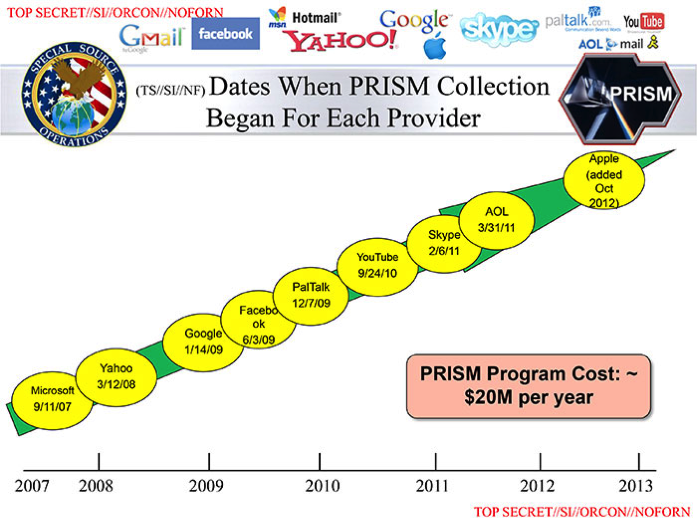
The initial story stated that Verizon, one of America’s major mobile service providers had been asked by the NSA to submit metadata to the government organisation. This metadata did not include the content of the calls made, but could help people establish the location and duration of a call. Further stories revealed that by receiving data from private technology based firms such as Google, Microsoft and seven others, NSA also had access to your Internet history, including your emails and other communication mediums. This not only violated privacy of users, but also threatened further misuse of this information. Labeled as PRISM, this classified information about Internet surveillance was brought in the public domain by a whistleblower named Edward Snowden – a 29-year old private contractor working with the NSA. As a heavy critique of the Obama government, the revelations of the story continue to unfold even today, with classified information still being released in bits and pieces.
The relevance of this story exists in the very threats technology is known to raise. It also raises validity of Paul Virilio’s concept of the theory of accident, stating that every technology comes with its accompanying accident. He states in The Original Accident “To invent the train is to invent the accident of derailment. To invent the domestic car is to produce the pile-up on the motorway”. What Virilio is suggesting with this theory of the accident is that technological progress can never be cast in simply or straightforwardly positive terms. The traditional ideology of progress would tell us that the history of technical development obeys an inevitable logic of incremental improvement.[2] Here surveillance has ended up being the accident of the communication of technologies glorified in the first two chapters. As single subject publications focusing on technology, it becomes a significant space to also criticise technology.
This chapter looks at how the four websites deal with this significant issue drawn around policy and surveillance within one week of The Guardian breaking the story (i.e. June 5-11, 2013). It draws parallels with the treatment of existing research and brings into notice original research carried out by them. Similar to Chapter 1, it also looks at the way headlines are worded and the information is sourced, in addition to the limitations of the coverage that is carried out.
Quantitative Analysis
“For years … it was like the number of articles to come out on NSA you could count on the fingers on one hand,” said James Bamford, who has written four books on government surveillance. “Now it’s almost impossible to keep up.”[3]
Despite having key technology based electronic shows such as Computex 2013 and Apple’s Annual World Wide Developers Conference 2013 (WWDC 2013) during the same time, the NSA leak accounted for around 10% of the coverage between June 5-11 on Gigaom and Techcrunch. The least amount of coverage was provided by Engadget with only 3% of the total 366 articles being devoted to the topic. The maximum coverage was provided by the Verge, with 12% of the total number of articles, being centered on the NSA leaks.
Sources
The credibility of any journalistic piece lies in the sources of the same. In the case of the NSA surveillance story, the news was broken by the Guardian and the Washington post and the primary source for their information was a set of documents leaked by former NSA contractor Edward Snowden. Although the identity of the NSA official behind the leaked documents was released on 9th June – four days after the initial story, using the secondary source of the initial report, the four websites carried out a report on the allegations. Moreover, they are seen to contact all the ten companies alleged to be involved in the PRISM controversy for official statements. Like other national and international news outlets, these statements resonate among each other with everyone denying any involvement in the program. They state that they had not provided ‘direct access of their servers’ to any government organisation.
Apart from these, another source that overlaps the four portals is Twitter. Clearly, the revelations in this case sparked a huge level of debate on social media. With user privacy being compromised, Internet experts, journalists and political figures were brought into the foray with public statements they had made on spaces such as Twitter along with individual comments provided to the publication.
Breaking down the coverage
In Engadget’s 10 articles published, the website quotes the Guardian U.S. and Washington Posts for the claims that they make around phone call data collection and the PRISM program for Internet surveillance. In addition, follow up stories by the New York Times and the Wall Street Journal also act as the basis of further reportage. There is no editorial or opinion published about the issue.
Gigaom’s treatment of the subject brings in a combination hardcore reporting and analysis. Interestingly, the first story[4] published on the subject is an opinion rather than a report. One that with the author’s casual usage of the pronoun ‘I’, revolves along the lines of personal analysis and assumes that the reader already knows about the scandal. The headline of the same, “Will the latest NSA surveillance scandal be a wake-up call about the power of data?” only reiterates this assumption. The second article however, brings in original speculation in the slew of theories floating in the media. Using original work, the piece[5] gives a possible way with which the NSA might be analyzing this multitude of call data. Another key piece titled “The NSA surveillance story reinforces why an entity like WikiLeaks is so important” by Mathew Ingram outlines the importance of whistleblowers by tracing back to the Pentagon Papers, Wikileaks and now NSA, and quotes tweets of the journalist behind the NSA story – Glenn Greenwald. Coming to the allegations against technology companies based out of the US, though the report is picked from the slides leaked by The Washington Post[6], all companies are contacted individually by Gigaom and their responses are published in full.[7]
Out of the 18 pieces that were published, 11 can be characterised as Op-Ed pieces bordering on theories around how certain surveillance operation might be being carried out, the journalistic endeavor of bringing out such a story and the dilemma that an everyday Internet user is bound to face in such a situation. Some of the titles of these stories are:
Lessons from PRISM: Sometimes it’s better not to be part of the media establishment
For web users around the world, everything is different now
Welcome to the new world of passive surveillance
Another piece titled “NSA spying fallout: expect big impact in Europe and elsewhere” follows no tenets of objectivity, with the author’s opinion strewn all over the place. Here is an excerpt from the beginning of the article:
UPDATE: I’ll admit I am shocked to have received this response from the European Commission’s Home Affairs department to my request for comment, with particular regard to the impact on EU citizens’ privacy: “We do not have any comments. This is an internal U.S. matter.” For the reason behind my surprise, read on…
UPDATE 2: Less blasé reactions are now starting to roll in. That link will also take you to a revised statement from the European Commission, which now concedes this may not be just an internal U.S. matter.
This is a great day to be a conspiracy theorist. Vindication! The National Security Agency – part of the U.S. military – reportedly has a direct line into the systems of some of the world’s biggest web and tech companies, all of which are of course sited in the U.S.
The opening statement of the article that works towards making the reader stick to the article is a rather non-conventional approach to journalism. With the author bringing his own strong opinions and combining it with news, it sways away from the tenets of objective unbiased reporting.
Techcrunch’s work around the topic has seen factual inaccuracies and sensationalism emerge as key issues in their journalistic pursuit. The first mistake was pointed out by a reader when ‘leaked’ tags were attributed to already public documents by the publication[8]. After a reader pointed out the error in the comments (as seen in the image below), the publication went on to rectify its mistake.
In another article later titled “Doublespeak Denials Of PRISM Hid The Truth About Participation”[9], the headline was previously edited as it ‘went a bit far’. Here is the justification given by the author for the same:
This article and its headline have been edited as I think the title “Doublespeak Denials Of Prism Participation Were Careful Lies” went a bit far. The execs weren’t lying, but by denying specifics rather than discussing their participation in PRISM on a high level, I think they obscured their involvement. However, their companies are legally required to provide private information requested by the government, and were legally restricted in how they could explain the process, so I feel the blame rests more on the NSA than the tech giants.
TechCrunch’s sensationalistic approach that is seen in Chapter 1, carry forwards its legacy even while covering the NSA case. There is one story titled Who the NSA follows, on Twitter[10], that lists the accounts a seemingly NSA account (@NSACareers) is following on Twitter. The author says, “What is a surprise is that the only legit-seeming NSA Twitter account I can find only follows seven accounts.” It is a legit-seeming account and the author has no proof that it is a legit account – yet, a post is made about the same. What is noteworthy is that one of the key followers in the list is Mashable – one of Techcrunch’s competitors. This competition is also observed to play out in the rather unnecessary article that TechCrunch went on to publish. The article ends with the note – “Betrayed by all its M*shable reading, perhaps the NSA did not include Twitter in its PRISM program because the NSA does not know how to use Twitter?”
The culture of speculation continues in another news story titled President Obama Visiting Silicon Valley Tonight, As Reports Of NSA’s Tech Spying Come To Light, the author quotes President Obama’s official schedule and mentions the fact that Air Force One is en route to the San Francisco Bay area hours after the NSA revelations have been brought into light. Although the publication mentions that he is visiting the city for a $32,400 per person dinner at the home Sun Microsystems’ CEO, Vinod Khosla, in ends by saying, “But given the latest news and how it’s absolutely dominating the discussions in the tech world right now, it seems inevitable that tonight’s conversations will go a bit off-topic from those planned talking points.” This is not the only story that has been published unnecessarily. Staff Writer John Biggs elaborates on the possibility of the value of Bitcoin falling due to the NSA leaks in one news report.[11] The story lacks facts written based on plausible theories with the author stating, “The correlation between price (in this case the price of Bitcoin) and the PRISM news making the rounds this weekend – while not airtight – is at least plausible.”
In terms of quantity, The Verge provided the maximum number of articles (out of the four websites being analysed) about the NSA leaks. However, moving towards quality, their reportage is the most repetitive when compared to the other three. The first story[12] published carries all necessary information about the Verizon NSA deal and how Verizon was providing call data enmasse to the intelligence agency. Similar to other publications, it quotes a response from Verizon. Later on, a follow up story[13] is published with the official statement of government officials. However, it is repetitive. The story whose word count just falls short of 200 words has less than 80 words of new information to add. The rest of the story is picked up from the previous report. There is one report to list the companies involved in PRISM and their statements. When the CEOs of these firms made their own public statements further on, separate stories have been devoted to each. Since, there isn’t anything new that these leaders are adding, again, the reportage is repetitive.
The Update
The first two chapters didn’t experience ‘the update’ to a huge extent. How the Internet differs from a print story, is that one can edit it after filing the story. This feature is often used to meet the needs of speed reporting, when the reporter might fail to receive responses in time. Since the NSA leak was a story in the domain of ‘Breaking News’, speed played a crucial role in the reportage. All news portals that carried out independent research published several stories mid-way, stating that they would update it as further developments are made. For instance, after Washington Post published the slides revealing the names of the tech giants involved (as mentioned earlier in the chapter), all three websites published a story minutes after the initial report. However, these stories were then updated with additional information that independent research enabled them to obtain.
The AOL angle
As mentioned in the introduction, two of the publications in the analysis – namely, TechCrunch and Engadget, come under the same media house. This media company called America Online (popularly known as AOL) is also one of the technology ten firms that were alleged to be involved in PRISM scandal. Due to the same, both publications carried a disclosure in the initial stories to explicitly mention that their parent company is one of the accused in the report.
The man behind the story: Edward Snowden
The first rendezvous was in Kowloon’s Mira hotel, a chic, modern edifice in the heart of the tourist district. Poitras and Greenwald were to meet Snowden in a quiet part of the hotel, next to a large plastic alligator. They would swap pre-agreed phrases. Snowden would carry a Rubik’s cube.
Everything Greenwald knew about Snowden pointed in one direction: that he was a grizzled veteran of the intelligence community. “I thought he must be a pretty senior bureaucrat,” Greenwald says. Probably 60-odd, wearing a blue blazer with shiny gold buttons, receding grey hair, sensible black shoes, spectacles, a club tie. Perhaps he was the CIA’s station chief in Hong Kong.
The pair reached the alligator ahead of schedule. They sat down. They waited. Nothing happened. The source didn’t show. Strange.
If the initial meeting failed, the plan was to return later the same morning. Greenwald and Poitras came back. They waited for a second time.
And then they saw him – a pale, spindle-limbed, nervous, preposterously young man. He was dressed in a white T-shirt and jeans. In his right hand was a scrambled Rubik’s cube. Had there been a mistake?
The young man – if indeed he were the source – had sent encrypted instructions as to how the initial verification would proceed:
Greenwald: What time does the restaurant open?
The source: At noon. But don’t go there, the food sucks…
Greenwald – nervous – said his lines, struggling to keep a straight face. Snowden then said simply, “Follow me.” The three walked silently to the elevator. They rode to the first floor and followed the cube-man to room 1014. Optimistically, Greenwald speculated that he was the son of the source, or his personal assistant. If not, then the encounter was a waste of time, a hoax.
Over the course of the day, however, Snowden told his story. He was, he said, a 29-year old contractor with the National Security Agency. He had been based at the NSA’s regional operations centre in Kunia on the Pacific Island in Hawaii. Two weeks ago he had quit his job, effectively abandoned and bid farewell to his girlfriend, and secretly boarded a flight to Hong Kong. He had taken with him four laptops.
The laptops were heavily encrypted. But from them Snowden had access to documents taken from NSA and GCHQ’s internal servers. Tens of thousands of documents, in fact. Most were stamped Top Secret. Some were marked Top Secret Strap 1 – the British higher tier of super-classification for intercept material – or even Strap 2, which was almost as secret as you could get. No one – apart from a restricted circle of security officials – had ever seen documents of this kind before. What he was carrying, Snowden indicated, was the biggest intelligence leak in history.[14]
Throughout the story and the discussion that has followed, Edward Snowden is the man who has been termed as a hero by many, alongside being labeled as a traitor as well. Majority of the debate that has been around the issue of privacy now revolves asking if Snowden has saved the world or jeopardized National Security by leaking classified information. In the months following the leak, Snowden has spoken publicly at various occasions and has been extremely vocal about his concerns and the reasons why he decided to turn into a whistleblower. When his identity was revealed through a video interview released by the Guardian on June 9, not much of this hype around the man had developed. He didn’t win Time’s Person of the Year award or rank in Google’s year-end list of top searches, but Edward Snowden repeatedly dominated Washington’s policy conversation in 2013—and he did so without ever setting foot there.
In this context, it is crucial to analysis how was reportage around this one man treated by the four websites under our analysis. Most interesting to note is that in the entire week of reports, The Verge never carried a photo of Edward Snowden. While all of them carried one story each after the release of Guardian’s video, except for the Verge, all three used a headshot of Snowden from the video to accompany their articles. These were titled:
NSA Whistleblower reveals himself: ‘ I don’t want to live in a society that does these things’(The Verge)
Spy Whistleblower comes forward, says “NSA routinely lies” (TechCrunch)
NSA Whistleblower revealed: 29 year old former CIA staffer says he felt compelled to leak (Gigaom)
PRISM Whistleblower Edward Snowden reveals himself (Engadget)
The importance of Snowden’s identity is one of the key factors of the story. While usually whistleblowers try to remain anonymous for as long as possible, Snowden’s identity is revealed within the same week as the leak. Yet, there is only one story on each portal that is dedicated to him. Even these lack facts revealed by Guardian in the original reports. For instance, although Engadget and Gigaom mention the name of the firm Snowden was directly working under (Booz Allen Hamilton) with a response from the company, the other two conveniently miss out on this crucial detail and label Snowden as a private NSA contractor.
Building on interactivity
For a story like the NSA leak that had new leads emerging every day, tracing the timeline can be a bit of a challenge. To combat this issue it is necessary that the interactive space of the Internet is used to its potential. Hence, weaving the narrative in segregated spaces becomes all the more important. This section aims to look at how the aforementioned goal is achieved by the four publications being analysed.
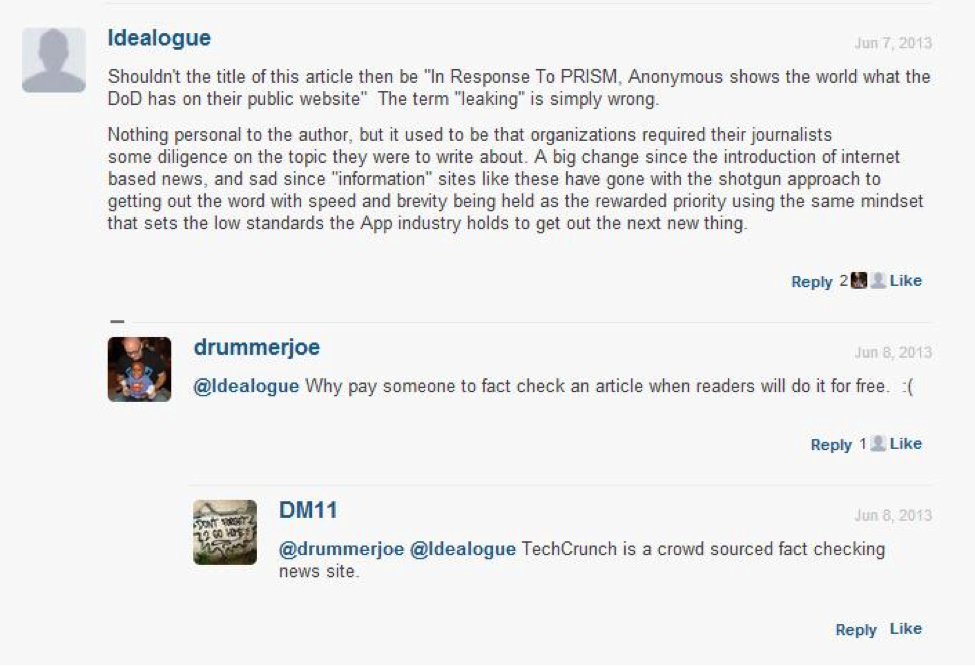
TechCrunch boasts of a section labeled CrunchGov under the tagline ‘where technology meets governance’. This section focusing on technology policy centered news is one of the core areas of the platform. Similar to the CrunchBase that exists for technology firms, for members of the House of Representatives, the website has a Tech Titans and Tech Threats section. Based on the policies of immigration, crowd funding, and an open Internet (SOPA), members are then given grades, where ranging from A to F. During the coverage of the NSA leaks, they used this table to quote and approach members such as Ron Wyden who are known to debate for an open Internet.
Gigaom built one post[15] to update the developments as and when they happened. One limitation of the same however is that the last update made to the story was the revealing of the whistleblower’s identity. Further developments to the NSA thread haven’t been updated. The Verge, used their platform to build a series of updates of the story. Titled, “Government contractor leaks massive surveillance effort by NSA, FBI on consumer services”, the post is one portal to track the NSA story from the latest update down to the oldest. As of 13th April, 2014, the total update count rests at 232.
Despite these efforts by the aforementioned websites, the landmark use of digital space with its team of developers and designers remains the Guardian’s multimedia feature – NSA files: Decoded. When it went live on November 1, the finished product – a six-part multimedia feature entitled NSA Files Decoded: What the revelations mean for you – was met with praise among the type of online journalism enthusiasts. Weaving together long form text, documentary-quality video interviews, embedded documents and interactive graphics, the story instantly generated a level of buzz not seen about a single piece of journalism since the New York Times published its Snow Fall piece last year.[16] The piece has talking heads of NSA representatives, government officials, Internet security experts and journalists adding to the narrative. The NSA leaks is traditionally Guardian’s story, such extensive form of interactive journalism is expected and justified. However, the websites under analysis fail to address similar story telling despite being single subject journalistic enterprises. It is however noteworthy that The Verge and Engadget wrote about Guardian’s comprehensive guide after its launch in November.
Conclusion
55 percent of American voters identified Edward Snowden as a “whistleblower” in July 2013
34 percent of American voters identified Snowden as a “traitor” in July 2013
40 days that journalists camped in the Moscow airport while Snowden waited for asylum
33 percent of Hong Kong residents consider Snowden “a hero”
956,107 YouTube views of “citizen journalism” video of arrest caught with Google Glass as of August 5
2 months’ (April and May 2012) worth of AP journalists’ phone records that the Justice Department seized in 2012[17]
The figures mentioned above clearly reflect on the importance the National Security Agency’s surveillance program holds for global citizens. It is an issue that goes beyond the American borders and one that has partaken to debates around privacy constantly. Hence, the way technology centric websites cover such policy issues is one aspect that is key to understanding their reporting strategy. While Engadget shifts focus to gadgets with the commencement of WWDC, and has a low number of posts dedicated to the NSA files, the other three devote a substantial amount to the then trending issue. TechCrunch is seen to continue more of a sensationalizing role that is previously observed in earlier chapters as well, while Gigaom continues to focus on political and social analysis. The Verge, ends up being highly repetitive – a deviation from its approach centered around exclusivity as seen in earlier chapters.
While mainstream publications such as The Guardian, New York Times, The Washington Post and Wall Street Journal are known to have uncovered crucial details in the NSA revelations, the same cannot be said for the websites being analysed. Although there is no dearth of conspiracy theories in this scenario – ones that are usually backed by other external conspiracy theories, only few hold some level of credibility. One of the few credible ones is Gigaom’s story suggesting the software being used for data analysis.
One debate that is seen missing in the range of varied analysis is that why should people care about surveillance. Much of the NSA’s defence is that the public should be unconcerned, summed up by the dictum: “If you have nothing to hide, you have nothing to fear.” But civil liberties groups such as the Electronic Frontier Foundation and the American Civil Liberties Union warn that surveillance goes well beyond what Congress intended and what the US constitution allows.[18] As commentary around policy is seen in the forum, it is mostly centered around why it happened, who did it, how journalism trumped over administrative secrecy and how we need more whistleblowers such as Snowden. Despite the study by Pew research that revealed public sentiment around Edward Snowden’s decision to leak these documents, there is a lack of effort on these publications’ end to explore the angle.
“Because even if you’re not doing anything wrong you’re being watched and recorded. And the storage capability of these systems increases every year consistently by orders of magnitude to where it’s getting to the point where you don’t have to have done anything wrong. You simply have to eventually fall under suspicion from somebody even by a wrong call. And then they can use this system to go back in time and scrutinize every decision you’ve ever made, every friend you’ve ever discussed something with. And attack you on that basis to sort to derive suspicion from an innocent life and paint anyone in the context of a wrongdoer.” – Edward Snowden
Footnotes
[1] Kirchner, Lauren. “Reporting in the Post-Snowden Era.” January 31, 2014. (accessed April 15, 2014).
[2]James, Ian. Paul Virilio. London: Routledge, 2007. p 115-116.
[3] Samuelsohn, Darren, and Dylan Byers. “The Snowden era of journalism.” POLITICO. (accessed April 10, 2014).
[4] Higginbotham, Stacey . “Will the latest NSA surveillance scandal be a wake-up call about the power of data?.” Gigaom. (accessed April 16, 2014).
[5] Harris, Derrick. “Here’s how the NSA analyzes all that call data.” Gigaom. (accessed April 15, 2014).
[6] The Washington Post. “NSA slides explain the PRISM data-collection program.” Washington Post. (accessed April 10, 2014).
[7] Kern, Eliza. “Silicon Valley companies deny reports U.S. government has “direct access” to their servers.” Gigaom. (accessed April 9, 2014).
[8] Perez, Sarah. “In Response To PRISM, Anonymous Leaks DoD Documents.” TechCrunch. (accessed April 10, 2014).
[9] Constine, Josh. “Doublespeak Denials Of PRISM Hid The Truth About Participation.” TechCrunch. (accessed April 10, 2014).
[10] Tsosis, Alexia. “Who The NSA Follows, On Twitter.” TechCrunch. (accessed April 11, 2014).
[11] Biggs, John. “Is PRISM Precipitating A Bitcoin Sell-Off?.” TechCrunch. (accessed April 11, 2014).
[12] Bishop, Bryan. “Leaked secret court order forces Verizon to hand over call records to NSA.” The Verge. (accessed April 11, 2014).
[13] Brian, Matt. “White House defends NSA as outrage over Verizon data surveillance grows.” The Verge. (accessed April 10, 2014).
[14] Harding, Luke. “Prologue: The Rendezvous.” The Snowden Files. London: Guardian Books, 2014.
[15] Ingram, Mathew. “Through a PRISM darkly: Tracking the ongoing NSA surveillance story.” Gigaom.
[16] Titlow, John Paul. “How Journalists At The Guardian Built That Epic NSA Story.” Co.Labs. (accessed April 10, 2014).
[17] Data sourced from Hard Numbers, Columbia Journalism Review, Dated. September 2013.